Learning C/C++ and Assembly may be the best thing for Offensive Security
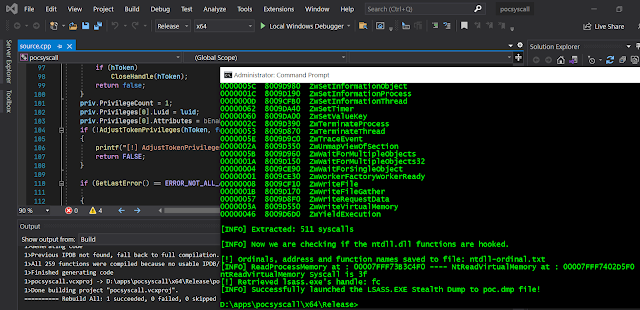
I read with interest how various Western Red Teams go through all lengths to get a single Mitre test working nicely, dumping lsass.exe. In addition, the Blue Teams have a lot of help in this area with EDRs aka expensive Endpoint Detection and Response software hitting all alerts when you even try to get near to lsass.exe process. Most of the red team companies do write great blogs documenting the efforts they put in their process dumpers. Obviously they will not share their secret sauce in a free blog. The logic is simple, why let their months of hard work go down the drain when some nice chaps will download their work to Virustotal or turn them into some machine learning generated signatures when the commercial EDR companies tow Virustotal for intelligence. If you read their blogs carefully, how do they fool the EDRs using merely C/C++? Yes, the mention syscall but they do not go reveal all their secrets easily. Ok, luckily my C/C++ and x86 Assembly are largely intact despi...